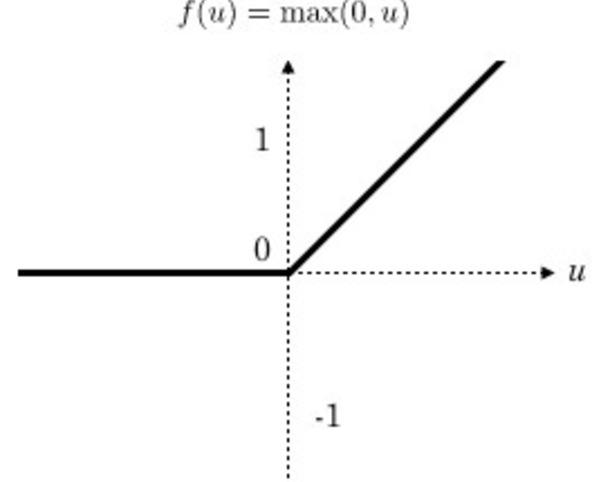Detection of Malware in Encrypted Traffic Using Deep Learning Neural Networks.
- 0 Collaborators
Encryption of the traffic ensures the confidentiality of the content, but it can make the network vulnerable to the malicious content that m ...learn more
Networking, Internet of Things, Artificial Intelligence
Groups
Student Developers for AI
Overview / Usage
Transport Layer Security(TLS) is the most sophisticated to handle all the security concerns of and above the transport layer. It is used to protect the confidentiality and privacy of upper-level application-level protocols like POP, HTTPS etc; This Protocol comes after the top application level, which means, unlike other protocols it operates at a higher level. TLS helps in establishment of encrypted connection between two parties
According to the recent research by Mozilla half of the traffic over the web is encrypted, and according to NSS labs research, 75% of the web traffic will be encrypted by the end of 2019. The encryption technology not only provided privacy and security to the communications over the web but also used as a leverage for the malicious threats over the web. With the increase in the encrypted traffic, there would be more chances of making our end-devices and servers vulnerable. It is observed that many of this malicious traffic is encrypted using the dominant transport layer security protocol. Which in turn has some complex data that is understandable and using which we can make deductions. We can use powerful Machine Learning Algorithms to classify the traffic over the web. This Machine Learning algorithm analyzes
the metadata transfer that takes place before the encryption of the communication begins, which means it analyzes the observable, un-encrypted data to makes deductions and classifies the data traffic between malicious and normal.
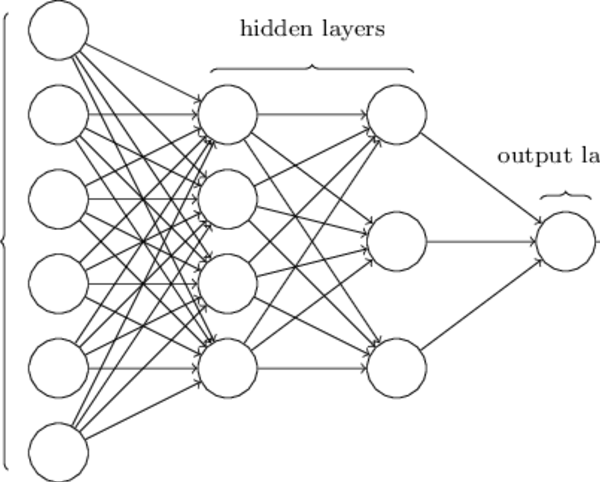
We use the Deep Learning Neural Network to classify the traffic over the web. These algorithms when applied or when put it into action they can act as tracer based on the deductions it made based on the complex data understandable to it. The features that are given to these algorithms would be the complex set of data that is being generated before the establishment of the encrypted communication channel.